WooYun-2014-79045:Supesite 前台注入 #3 (Delete)
漏洞作者: ′雨。
来源:http://www.wooyun.org/bugs/wooyun-2014-079045
简要描述
Delete 如果ucenter和supesite在一个裤的话 可以尝试把uckey注入出来 然后……
详细说明
在cp.php中
$ac = empty($_GET['ac']) ? 'profile' : trim($_GET['ac']);
if(in_array($ac, array('index', 'news', 'profile', 'credit', 'models'))) {
include_once(S_ROOT.'./source/cp_'.$ac.'.php');
包含进来
在source/cp_news.php中
if(empty($itemid)) { //这里让$itemid 不为空
if(!empty($_SCONFIG['posttime']) && $_SGLOBAL['group']['groupid'] != 1) {
if($_SGLOBAL['timestamp'] - $_SGLOBAL['member']['lastposttime'] < $_SCONFIG['posttime']) {
showmessage('post_too_much');
}
}
$newsarr['uid'] = $_SGLOBAL['supe_uid'];
$newsarr['username'] = $_SGLOBAL['supe_username'];
$newsarr['dateline'] = $_SGLOBAL['timestamp'];
if($_POST['fromtype'] == 'newspost') {
$newsarr['fromtype'] = 'newspost';
$newsarr['fromid'] = intval($_POST['id']);
} else {
$newsarr['fromtype'] = 'userpost';
}
if(!checkperm('allowdirectpost')) {
$itemarr['itemid'] = inserttable('spaceitems', $newsarr, 1);
inserttable('spacenews', $itemarr);
getreward('postinfo');
postspacetag('add', $_POST['type'], $itemarr['itemid'], $tagarr,1);
$do = 'pass';
} else {
$itemarr['itemid'] = inserttable('postitems', $newsarr, 1);
inserttable('postmessages', $itemarr);
postspacetag('add', $_POST['type'], $itemarr['itemid'], $tagarr,0);
$do = 'me';
}
//更新用户最新更新时间
if($_SGLOBAL['supe_uid']) {
updatetable('members', array('updatetime'=>$_SGLOBAL['timestamp'], 'lastposttime'=>$_SGLOBAL['timestamp']), array('uid'=>$_SGLOBAL['supe_uid']));
}
} else { //进入else
if(empty($_SGLOBAL['supe_uid'])) showmessage('no_permission');
updatetable('postitems', $newsarr, array('itemid'=>$itemid));
updatetable('postmessages', $itemarr, array('itemid'=>$itemid));
$itemid = empty($_POST['oitemid']) ? $itemid : $_POST['oitemid'];//没有intval
postspacetag('update', $_POST['type'], $itemid, $tagarr, 0);//跟这里
}
function postspacetag($op, $type, $itemid, $tagarr, $status) {
global $_SGLOBAL;
$deletetagidarr = $addtagidarr = $spacetagidarr = array();
if($op == 'add') { //已经存在的tag,执行加入操作
if(!empty($tagarr['existsid'])) {
$addtagidarr = $tagarr['existsid'];
$_SGLOBAL['db']->query('UPDATE '.tname('tags').' SET spacenewsnum=spacenewsnum+1 WHERE tagid IN ('.simplode($tagarr['existsid']).')');
}
} else {
$query = $_SGLOBAL['db']->query('SELECT * FROM '.tname('spacetags').' WHERE itemid=\''.$itemid.'\' AND status=\''.$status.'\'');//查询
while ($spacetag = $_SGLOBAL['db']->fetch_array($query)) {
if(!empty($tagarr['existsid']) && in_array($spacetag['tagid'], $tagarr['existsid'])) {
$spacetagidarr[] = $spacetag['tagid'];
} else {
$deletetagidarr[] = $spacetag['tagid'];//赋值
}
}
foreach ($tagarr['existsid'] as $etagid) {
if(!empty($spacetagidarr) && in_array($etagid, $spacetagidarr)) {
} else {
$addtagidarr[] = $etagid;
}
}
if(!empty($deletetagidarr)) {
//这里要$deletetagidarr不为空
那么也就是要让
$query = $_SGLOBAL['db']->query('SELECT * FROM '.tname('spacetags').' WHERE itemid=\''.$itemid.'\' AND status=\''.$status.'\'')这个查询出来的有内容
$_SGLOBAL['db']->query('DELETE FROM '.tname('spacetags').' WHERE itemid='.$itemid.' AND tagid IN ('.simplode($deletetagidarr).') AND status=\''.$status.'\'');//这里delete查询 WHERE itemid='.$itemid.' 没有被单引号引住。。 并且没intval导致注入
$_SGLOBAL['db']->query('UPDATE '.tname('tags').' SET spacenewsnum=spacenewsnum-1 WHERE tagid IN ('.simplode($deletetagidarr).')');
}
首先我们注册一个会员 然后投稿
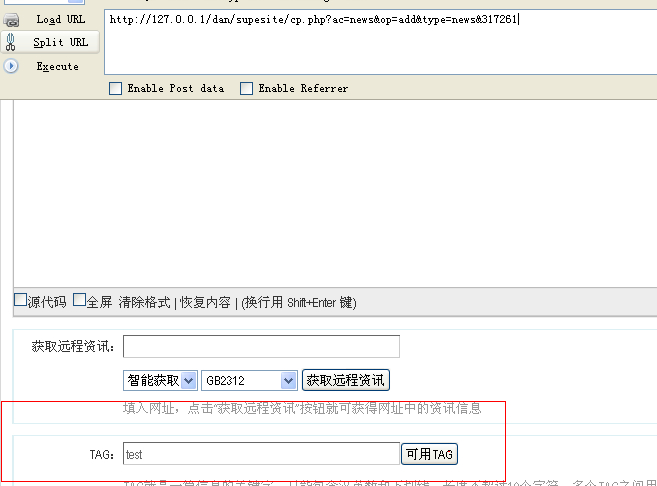
投稿 这里tag 随便写一个
+--------+-------+------------+------+--------+
| itemid | tagid | dateline | type | status |
+--------+-------+------------+------+--------+
| 3 | 1 | 1412680532 | news | 0 |
| 4 | 2 | 1412680930 | news | 0 |
数据库里也就创建了。。
这里的itemid 在.../dan/supesite/cp.php?ac=news&op=view&itemid=4
地址中就能看到为4
然后在$query = $_SGLOBAL['db']->query('SELECT * FROM '.tname('spacetags').' WHERE itemid=\''.$itemid.'\' AND status=\''.$status.'\'');
这里查询
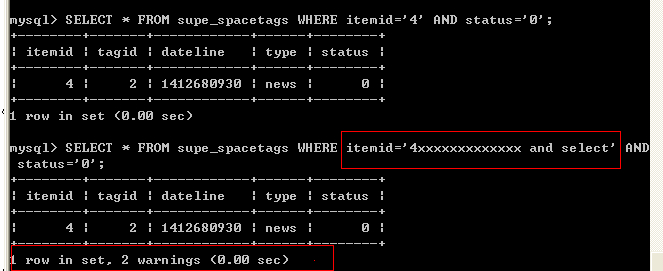
这里查询 后面虽然跟了一些字符 提示warning 但是还是能查询出来。
$_SGLOBAL['db']->query('DELETE FROM '.tname('spacetags').' WHERE itemid='.$itemid.' AND tagid IN ('.simplode($deletetagidarr).') AND status=\''.$status.'\'');
然后就进来delete 里面没单引号 且无intval 导致注入。
投稿的时候抓包一下
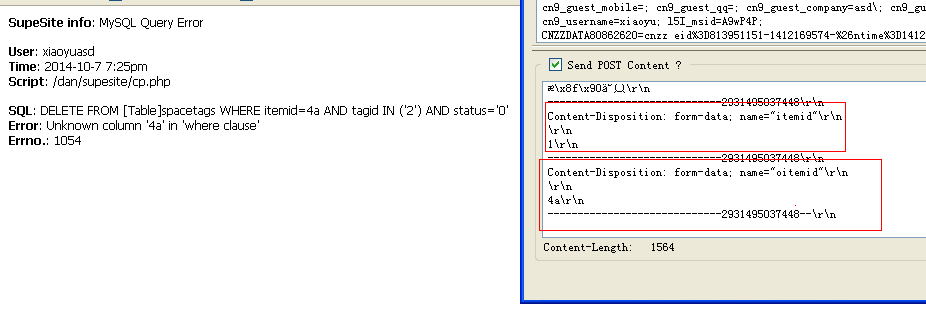

成功出数据
漏洞证明

修复方案
intval 或者 单引号上把